Internet Small Computer System Interface (iSCSI)
The Internet Small Computer System Interface is a transport protocol that allows SCSI communication between two nodes over IP-based networks. However, as you’ll remember, the SCSI protocol uses block-based storage communication (that is, the data is divided into blocks and communicated). For this purpose, iSCSI uses TCP for secure and reliable communication. iSCSI encapsulates the SCSI commands in TCP segments, which are then put in IP packets and routed through the network to the destination. As the iSCSI uses the IP networks, which are less expensive than separate, dedicated SAN fabrics, it allows for cost-optimization in the data centers.
iSCSI is implemented either through software-based drivers or in the hardware of the NICs, and it is capable of discovering iSCSI nodes and booting from an iSCSI storage system.
The iSCSI protocol supports IPsec for secure connectivity as well as authentication.
Because iSCSI allows for the communication between hosts that use the SCSI protocol over a network, using TCP as a transport, there are some additional concepts and characteristics to allow for the encapsulation and de-encapsulation of that traffic.
The network entities in the iSCSI communication are as follows:
- iSCSI initiator: This is the server/host that wants to use the resources of a storage system
- iSCSI target: A storage system that can communicate using the iSCSI protocol
Each iSCSI network entity contains an iSCSI node, which can be either an initiator or a target. The iSCSI node is identified by an iSCSI node name.
The iSCSI node needs to be capable of utilizing the IP network that’s connected to the iSCSI network entity to which it belongs. For this, the so called “network portal” is used. This component has network access, supports TCP/IP, and is identified by an IP address. Usually this is the network adapter, which can also be a wireless one.
Here, you can clearly see the different layers of processing data with iSCSI. The iSCSI node takes care of the mapping and encapsulation between the SCSI protocol and the underlying TCP transport protocol. The iSCSI node can be considered an overlay virtual component on the top of the network portal. The concept is shown on Figure 10-16.
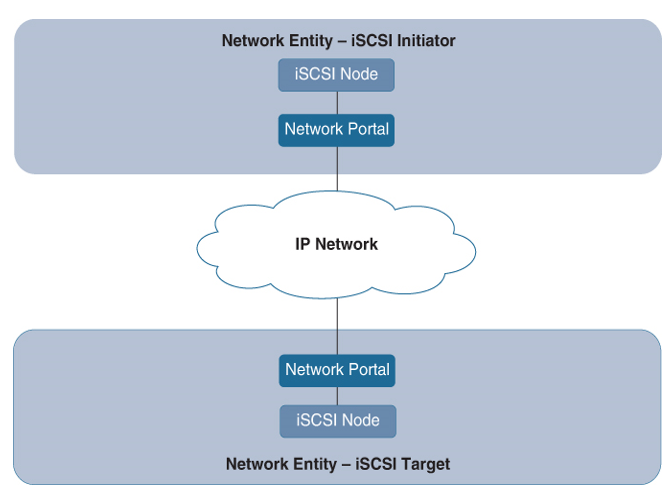
Figure 10-16 iSCSI Concepts
The iSCSI nodes use specific addressing known as iSCSI node names. The size of the node names can be up to 255 bytes. They need to use UTF-8 encoding in a human-readable string. They are used for target discovery and for login and authorization purposes.
The iSCSI node names are available in three formats:
- iSCSI Qualified Name (IQN), defined in RFC 3720, is one of the most popular types of iSCSI addressing. The fields in an IQN carry the following information:
- It always starts with “iqn”.
- The date the domain was acquired (in yyyy-mm format)
- The reversed domain name of the authority
- An option prefix of “:”.
- A text-based identifier defined by the naming authority
- Extended Unique Identifier (EUI), which consists of the following information:
- It always starts with “eui”.
- A 64-bit address.
- T11 Network Address Authority (NAA), which has the following structure:
- It starts with “naa”.
- A 64- or 128-bit identifier.
Figure 10-17 compares the different types of iSCSI node names.
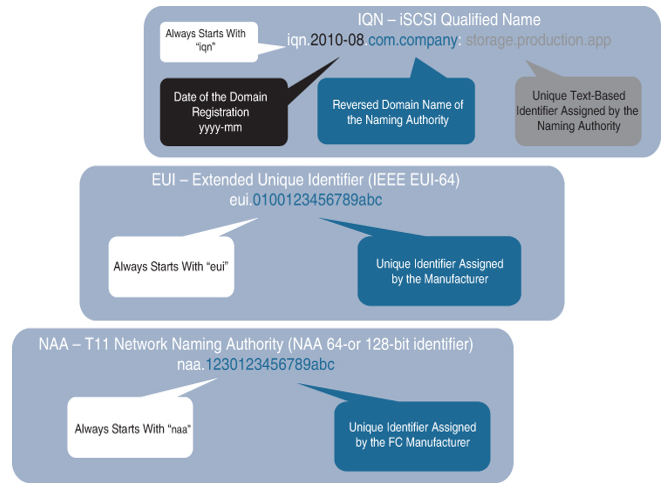
Figure 10-17 iSCSI Node Names
It is important to remember that the iSCSI communication relies on IP-based network communication, which means that the iSCSI initiator or target first has to be capable of communicating in the network; only then can iSCSI communication be established. That’s why the major components that are always needed are the IP address/hostname of the iSCSI network entity, the port number for the iSCSI communication (3260 to be allowed), the iSCSI node name, and an additional CHAP secret, if there is one.